Honeypot for Spammers

Last week I wrote about Chinese spammers and hackers. After the first shock I decided to install a Honeypot for Spammers. It worked wonderfully.
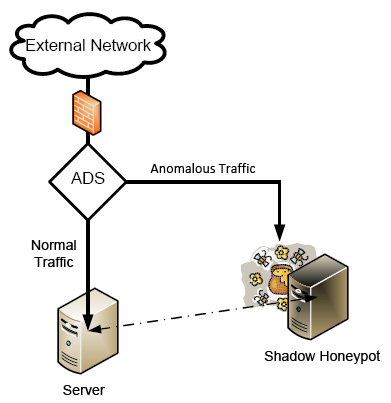
The definition of a Honeypot
“A server that is configured to detect an intruder by mirroring a real production system. It appears as an ordinary server doing work, but all the data and transactions are phony. Located either in or outside the firewall, the honeypot is used to learn about an intruder’s techniques as well as determine vulnerabilities in the real system.”
How a Honeypot works
It’s been funny to watch the pot during 24 hours of activity. I had the ADS programmed to send me an alert when it detected somebody leeching on the pot. So I could observe the leecher/spammer in real time.
Unfortunately there had also been 2 really serious guys who knew a big bunch of tricks. One came from the USA (ENZUINC Cloud network). This one tried to bring in worms that could go up to root level. I knocked him out immediately and informed his ISP. The ISP is now after him …
The other one came from the Netherlands Noord-holland, Amsterdam. He changed his IP address at high speed and used nearly all network blocks of his provider (Ecatel Ltd.) Also this one I had to lock out immediately. This action may lock out many honest Dutch visitors. These are 0.23% of our visitors. I hope this Ecatel Ltd. can find the guy quickly and stop him forever. I would like to re-open the Dutch gate.
The worst are the Chinese and the Ukrainians
Dont’ cry – stop spam !
[GARD]
BTW: I am a CISSP




Sometimes coincidences exist: Just now we got a pot of honey from wild bees. Salamat po Suzy & Ralph